Network Address Translation (NAT) is a process in which one or more local IP addresses is translated into one or more Global IP address and vice versa in order to provide Internet access to the local hosts. Also, it does the translation of port numbers i.e., masks the port number of the host with another port number, in the packet that will be routed to the destination. It then makes the corresponding entries of IP address and port number in the NAT table. NAT generally operates on a router or firewall.
AWS NAT Gateways
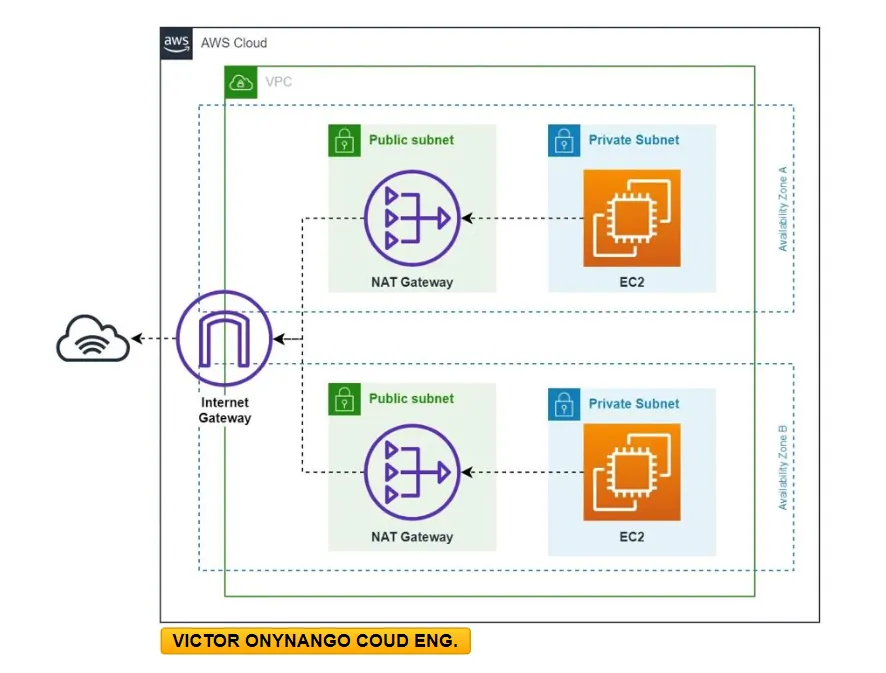
Amazon Web Services (AWS) NAT Gateway — stands for Network Address Translation. It is a managed AWS service that is scaled based on your usage. A NAT gateway allows instances in a private subnet to access the internet, while at the same time, preventing the internet from initiating connections with those instances.
When you create a VPC (Virtual Private Cloud) in AWS, you can choose to create one or more subnets. A subnet is a range of IP addresses in your VPC that you can use to launch your resources such as EC2 instances. Subnets can be public or private, depending on whether they have a route to the internet or not.
A private subnet does not have a direct route to the internet, which means that instances launched in that subnet cannot access resources on the Internet or be accessed from the Internet. To allow instances in a private subnet to access the internet, you can use a NAT Gateway.
Each NAT gateway is created in a specific Availability Zone and implemented with redundancy in that zone. There is a quota of 5 NGW the number of NAT gateways that you can create in each Availability Zone.
Note: NAT Gateway should always be associated with an Elastic IP.
A NAT Gateway is deployed in a public subnet and acts as a bridge between instances in the private subnet and the internet. When an instance in a private subnet sends a request to the Internet, the request is forwarded to the NAT Gateway, which replaces the instance’s private IP address with the NAT Gateway’s public IP address and sends the request to the Internet. When the response is received, the NAT Gateway translates the response back to the instance’s private IP address and sends it back to the instance.
By using a NAT Gateway, you can allow instances in a private subnet to access resources on the internet, such as software updates, patches, or external services, while at the same time, maintaining security by preventing the internet from initiating connections with those instances.
Types Of AWS NAT Gateways
Public NAT Gateways (Default)
Instances in private subnets can connect to the Internet through a public NAT gateway, but cannot receive unsolicited inbound connections from the Internet. You create a public NAT gateway in a public subnet and must associate an elastic IP address with the NAT gateway at creation. You route traffic from the NAT gateway to the internet gateway for the VPC. Alternatively, you can use a public NAT gateway to connect to other VPCs or your own-premises network. In this case, you route traffic from the NAT gateway through a transit gateway or a virtual private gateway.
Private NAT Gateways
Instances in private subnets can connect to other VPCs or your own-premises network through a private NAT gateway. You can route traffic from the NAT gateway through a transit gateway or a virtual private gateway. You cannot associate an elastic IP address with a private NAT gateway. You can attach an internet gateway to a VPC with a private NAT gateway, but if you route traffic from the private NAT gateway to the internet gateway, the internet gateway drops the traffic.
The main use case of NAT Gateway is to allow you to have Internet access in private subnets of your Virtual Private Cloud. This way your instances still can’t be accessed from the Internet but the instances themselves can access the Internet. So, you have Internet access without having a risk of being hacked through publicly accessible instances.
NAT Gateway entry in Route Table — In the private route table you need to make an entry for the NAT Gateway so that traffic generated from private instances can be routed via this route to the internet.
By default, users do not have permission to work with NAT gateways. You can create an IAM role with a policy attached that grants users permission to create, describe, and delete NAT gateways.
Work With NAT Gateways
Follow the below steps to create a Nat Gateway using the AWS console:
To create a Nat gateway first make sure you are in the region where you created the VPC.
Then in the search box, type VPC then select VPC under services.
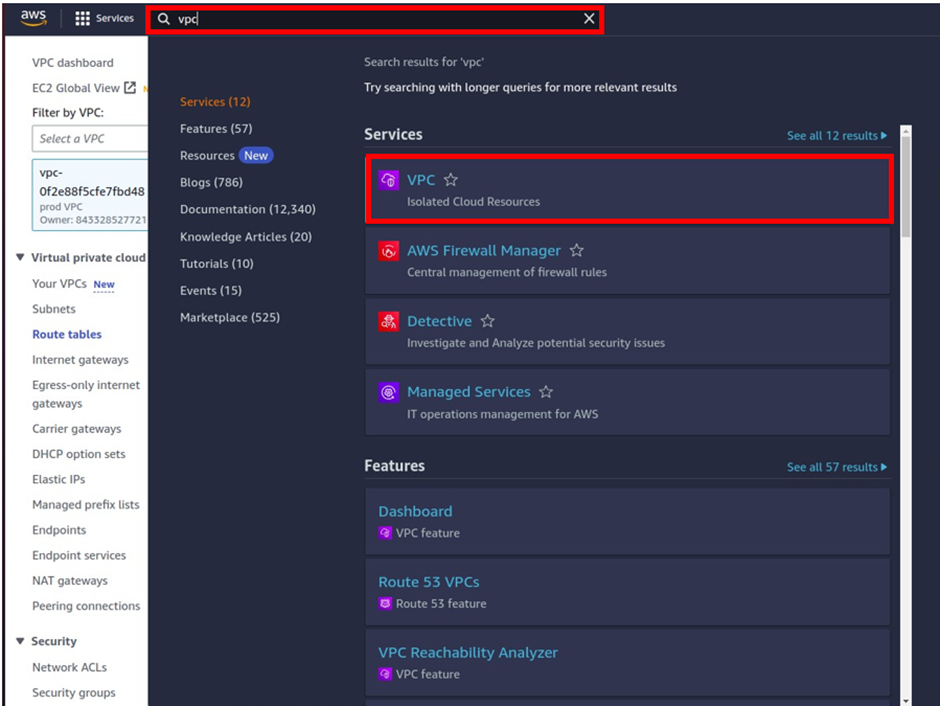
On the VPC dashboard on the left side of the navigation pane select Nat gateway, then click Create Nat gateway.
We will create the first Nat gateway in the public subnet az1.
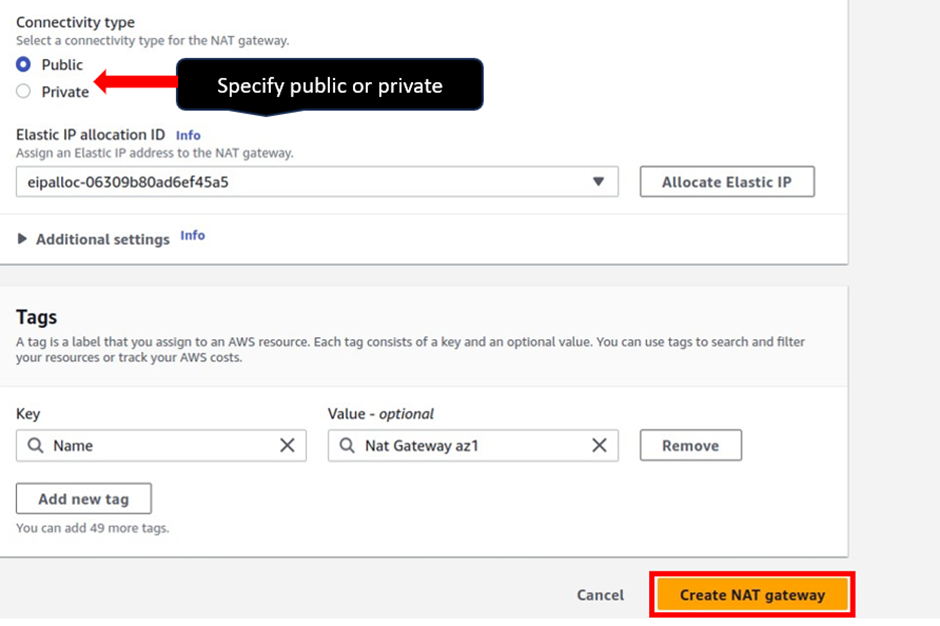
In the Create Nat Gateway dashboard under name give your Nat gateway name, call it Nat gateway az1. Once you’ve given your Nat gateway a name, select the subnet where you want to put your Nat gateway. so under subnet, select the drop-down and look for public subnet az1 then select it.
Scroll down, and under elastic allocation ID click allocate an elastic IP and that is going to allocate an elastic IP for you.
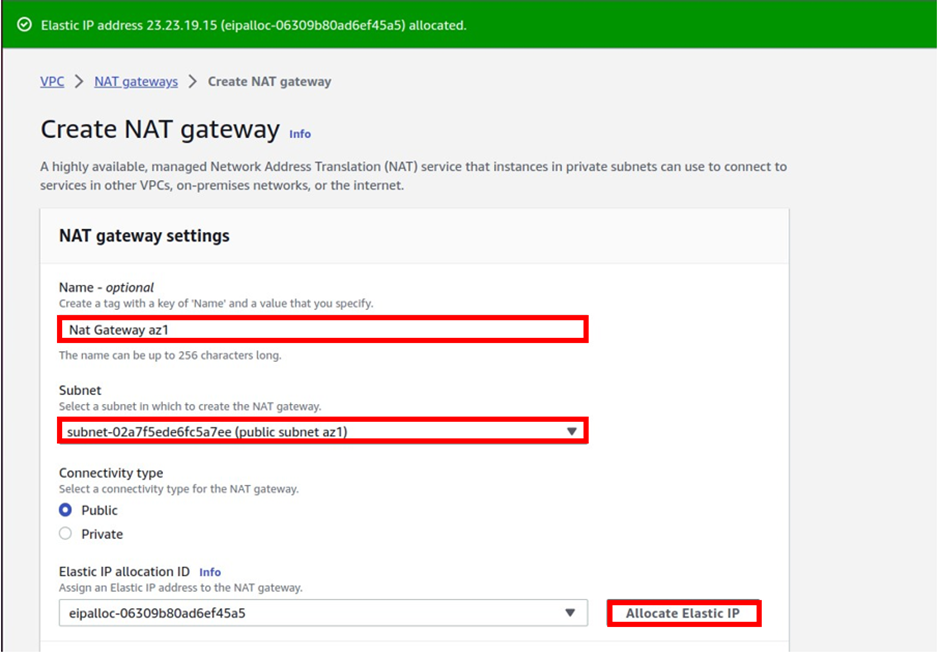
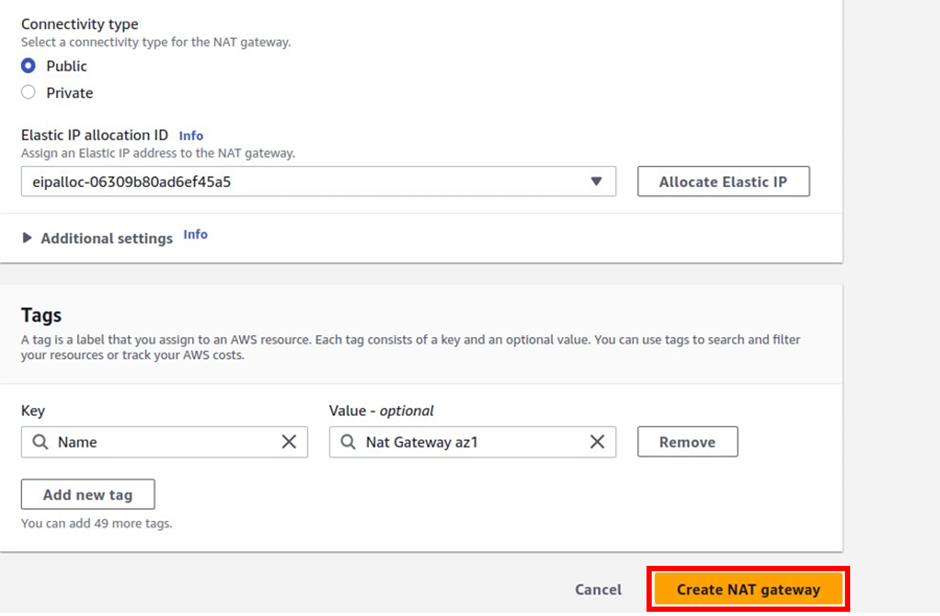
These are the only settings we need to create a Nat gateway, scroll down and click Create Nat gateway.
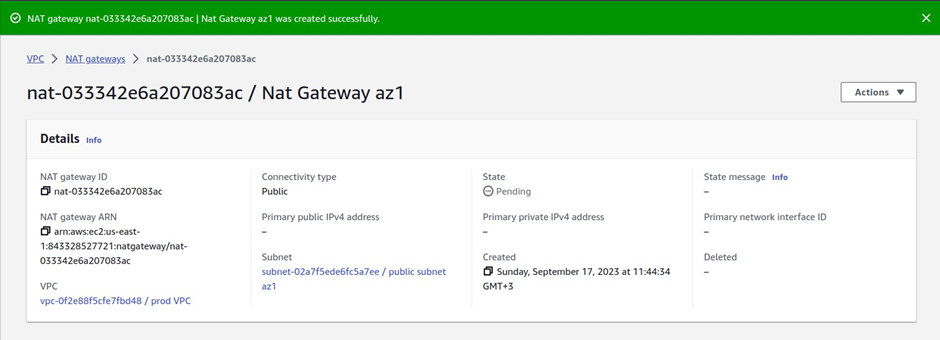
Success, we have created our first Nat gateway in the public subnet az1
Delete The AWS NAT Gateway
Deleting a NAT gateway disassociates its Elastic IP address, but does not release the address from your account. So again, make sure you release the elastic IP address from your account.
Stay tuned for more.
Thank you!

A skilled Cloud DevOps Engineer and Solutions Architect specializing in infrastructure provisioning and automation, with a focus on building scalable, fault-tolerant, and secure cloud environments.