A NAT (Network Address Translation) allows instances in a private subnet to access the internet or other AWS services without exposing them to inbound traffic from the public internet. It translates private IP addresses to public IP addresses for outbound traffic, ensuring a secure and controlled flow of data between internal resources and the external world.
Project objective
In this project, will create two NAT Gateways in two public subnets in different availability zones.
We will then create two Route Tables; we will add a public route to our private route tables to route traffic to the internet through the NAT gateways. This makes sure that our resources in the private subnets do not have direct communication to the internet.
The first Route Table will be routing traffic to the internet through the NAT Gateway in the first availability zone and will be associated with the two private subnets, the application subnet, and the database subnet in the first availability zone.
The second Route Table will be routing traffic to the internet through the NAT Gateway in the second availability zone and will be associated with the app and database subnets in the second availability zone.
This project will be achieved through a custom VPC, which I had provisioned earlier, to access the custom VPC, click here.
Project Implementation.
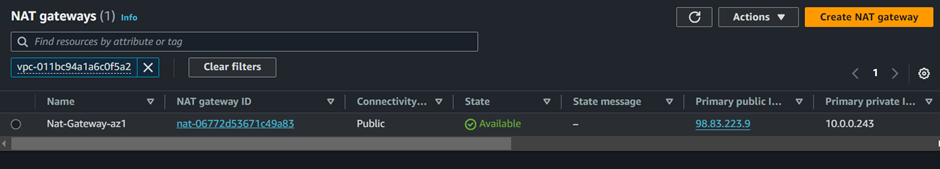
To create a NAT Gateway, navigate to the VPC dashboard and make sure you are in the region where you created your VPC. In the VPC dashboard in the left side UI select Nat Gateways.
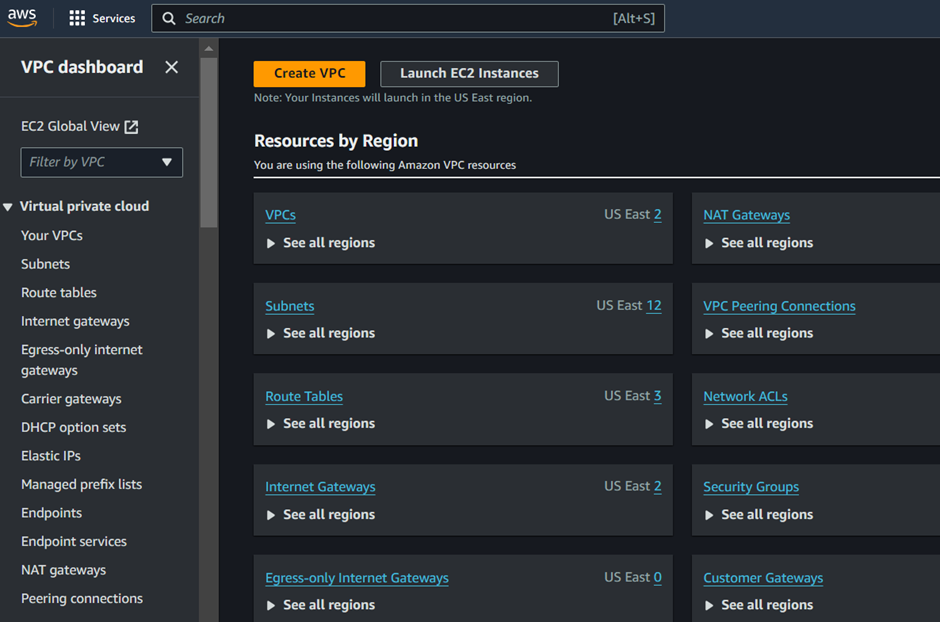
Click Create NAT gateway.
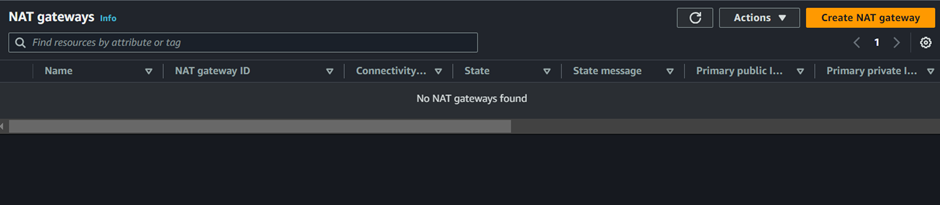
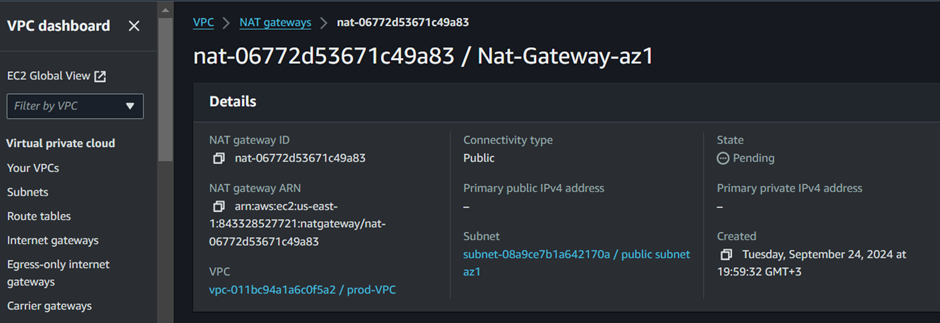
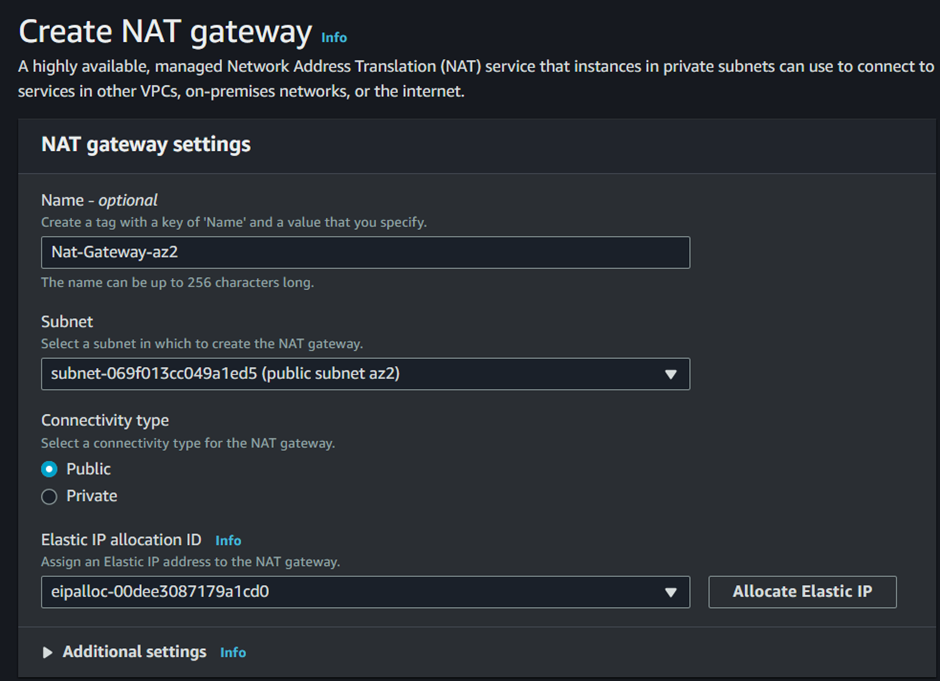
In the create NAT Gateway UI, fill in your details, we will create this NAT gateway in the first availability zone, so we will call it NAT gateway az1.
For the availability zone, select the drop-down button and select public subnet az1. Connectivity is public, then for elastic IP allocation ID, select allocate Elastic IP, this will allocate an Elastic IP for you.
Those are the only settings we need to create our NAT gateway, scroll down and click Create NAT gateway.
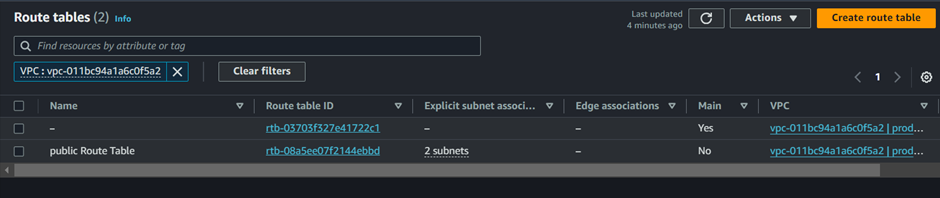
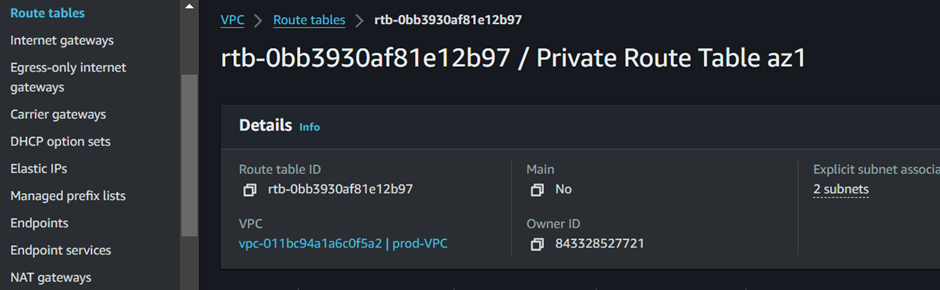
Our NAT gateway is successfully created. Next is to provision our first route table. On the left side of the VPC UI, select Route Tables.
Click Create route table.
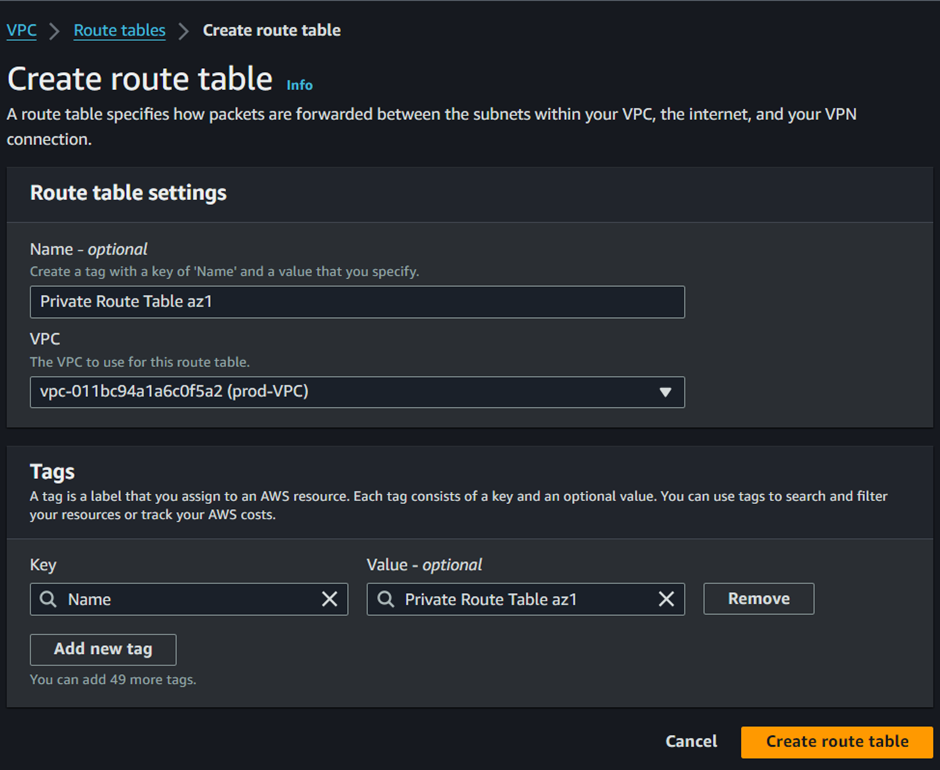
Fill in your route table details, call this route table private route table az1, and make sure to select your custom VPC in the drop-down button under VPC. Scroll down and click Create Route table.
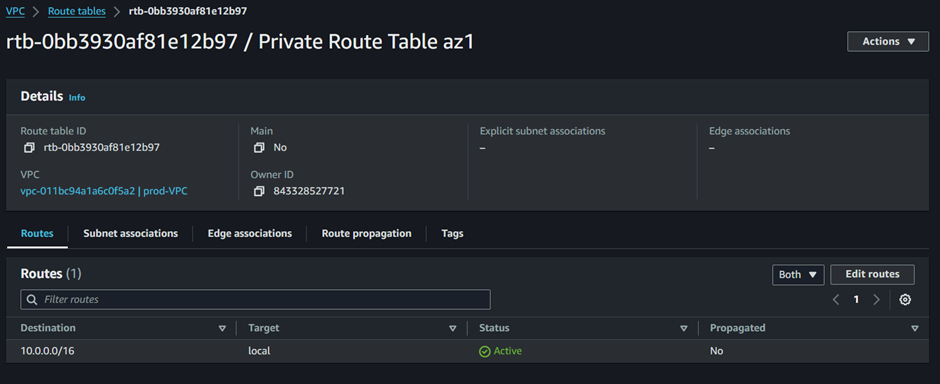
Our route table has been successfully created.

Currently, our route table is only routing traffic locally within the VPC. We will add a route to our route table. To add a route to this route table, navigate to the Routes tab then click Edit routes.
In the edit routes dashboard, click add route.
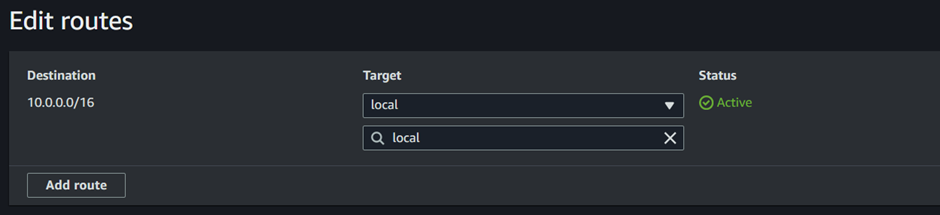
The public route to the internet is always 0.0.0.0/0 under destination, type in this value. We will direct this route to our NAT gateway, under target, select the drop-down button and select Nat gateway, make sure you select NAT gateway but not internet gateway. After selecting Nat gateway select the NAT gateway az1 you created previously and click save changes.
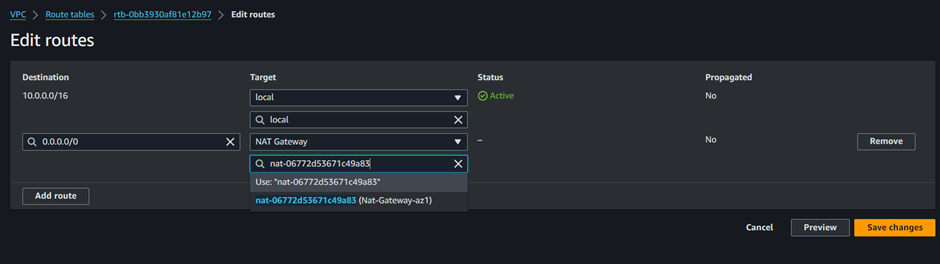
Our route table has been successfully updated.

If you look at the routes tab, we can see the Destination is 0.0.0.0/0 and the Target is the NAT gateway.
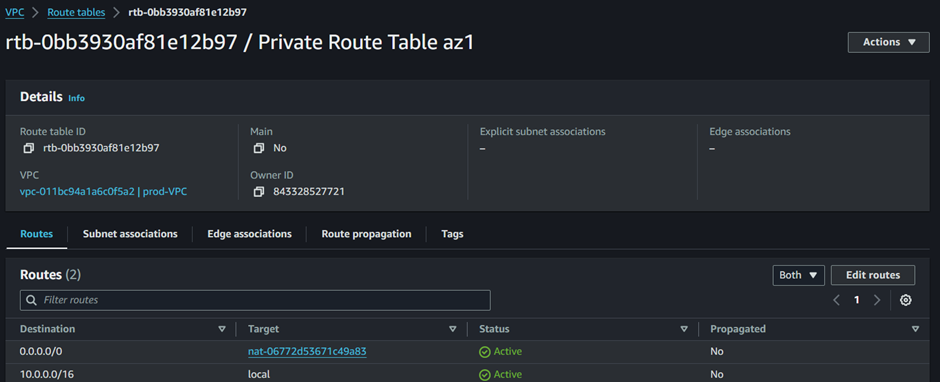
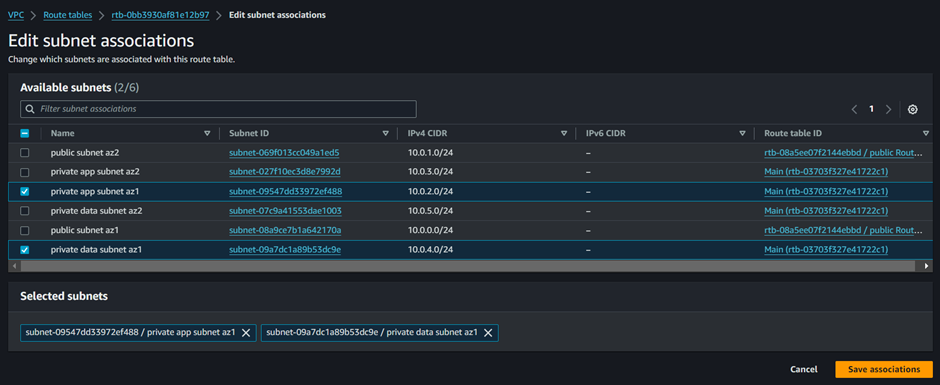
To associate this root table with the subnets, navigate to the subnet association tab then click edit subnet associations.
In the edit subnet associations select private app subnet az1 and private data subnet az1 then click save associations.
We will create the second NAT gateway, and click NAT gateways in the left UI.
Click Create NAT gateway.
In the NAT gateway dashboard, fill in the details, because we are launching this NAT gateway in the second availability zone, call it Nat gateway az2. Under subnet select public subnet az2 then scroll down and click allocate elastic IP, these are all the settings we need to create the second NAT gateway. Click Create NAT gateway.
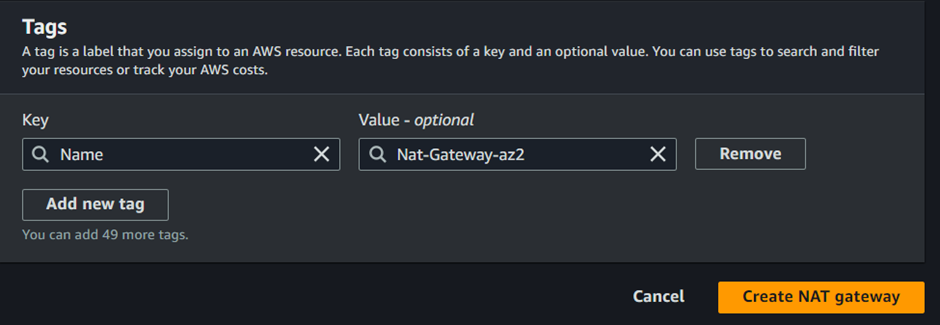
The second NAT gateway was successfully created. Next is to create the second Route table, click Route Tables.
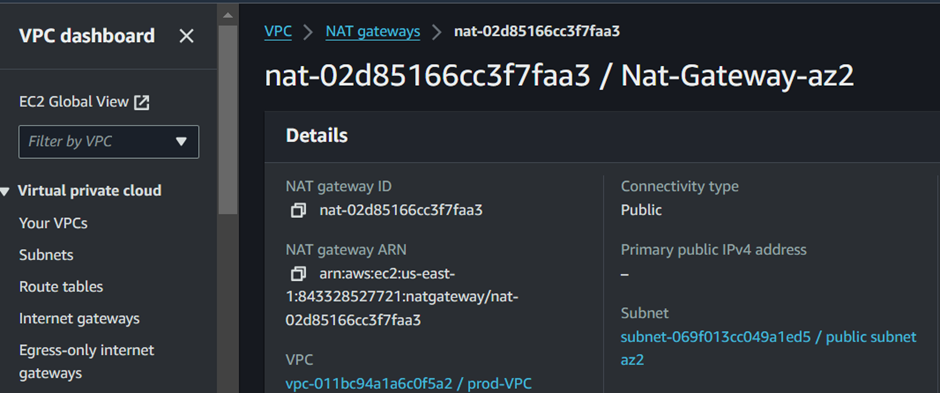
Call your route Table Private Route Table az2, select your VPC, then scroll down and click Create route table.
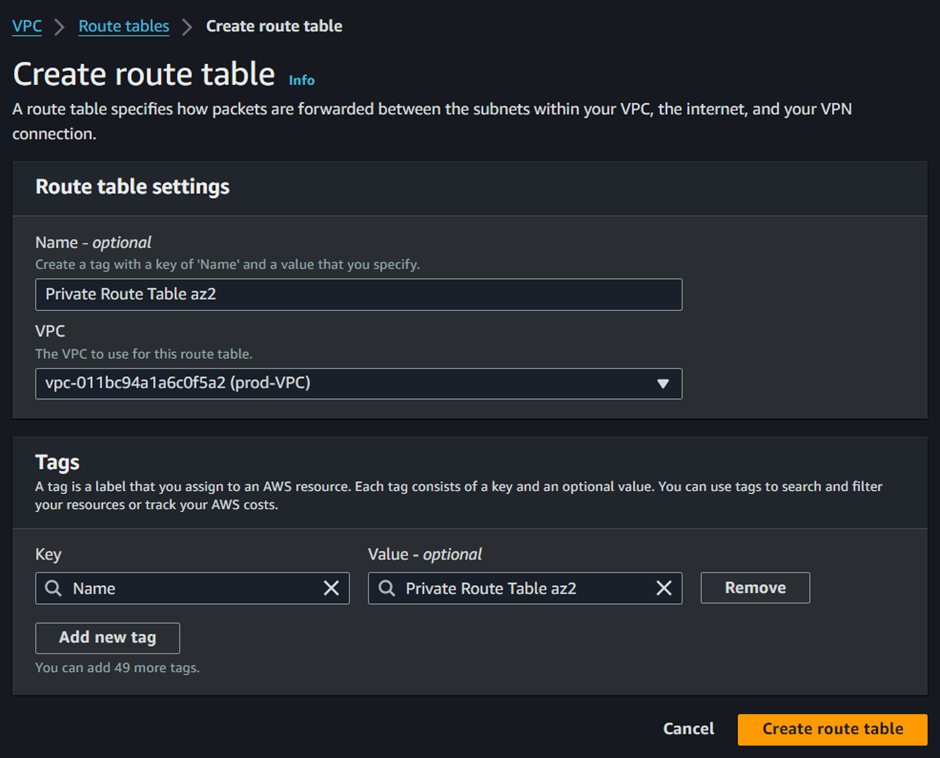
Move to the routes tab, then click edit routes, then add route.
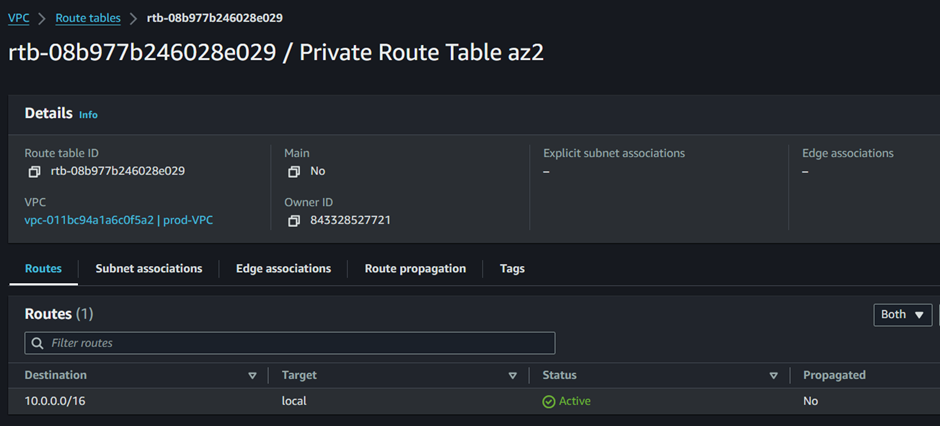
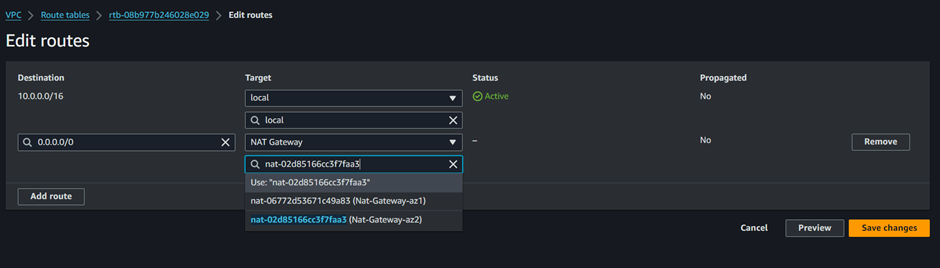
To add a public route to this route table to route traffic through the second NAT gateway in the second AZ, under destination add the public route 0.0.0.0/24 then under Target select Nat gateway then make sure you select the second Nat gateway.
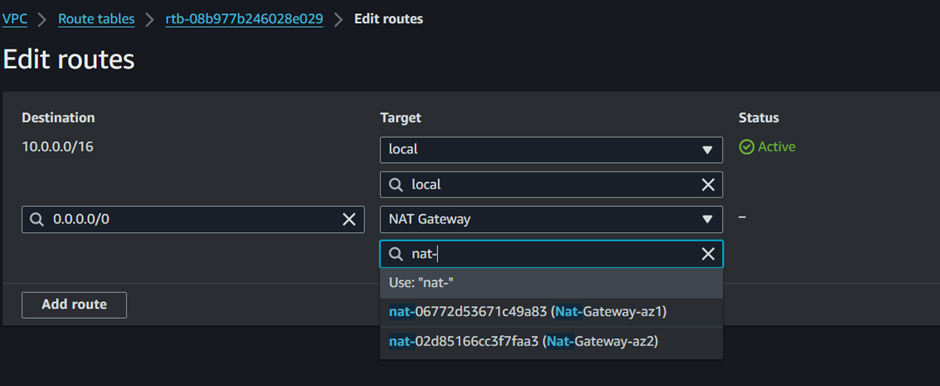
Click save changes.
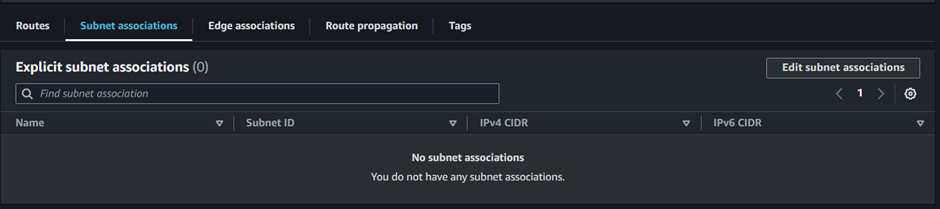
To associate this route table with our subnets, move to the subnet association tab then click edit associations.
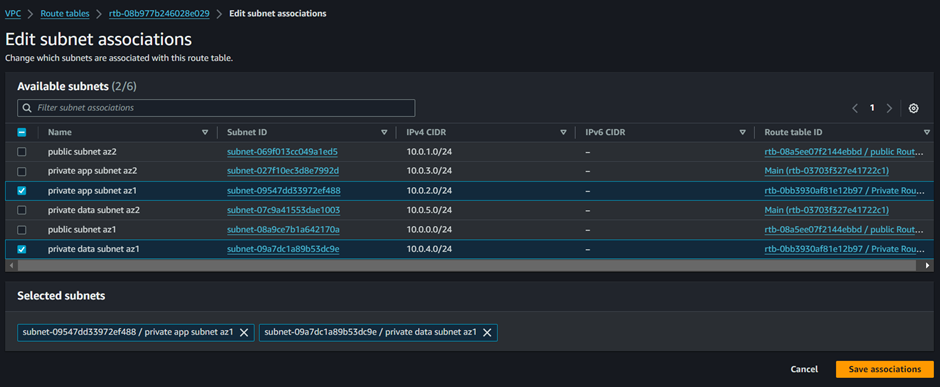
Select your subnets then click Save Associations.
That is for NAT gateways.
Conclusion
In summary, a NAT Gateway is essential for enabling secure internet access for instances in private subnets while maintaining network isolation. It helps organizations achieve better security and resource management by controlling inbound and outbound traffic in their cloud environments.
Thanks for reading and stay tuned for more.

A skilled Cloud DevOps Engineer and Solutions Architect specializing in infrastructure provisioning and automation, with a focus on building scalable, fault-tolerant, and secure cloud environments.

